Goodbye PodSecurityPolicy, Hello OPA Gatekeeper
The recently released version of Kubernetes v1. 25 removed the ‘PodSecurityPolicy (PSP)’ capability.
Read Now

In a previous blog post, we described how OPA Gatekeeper can be leveraged to enforce policies and strengthen governance in Kubernetes environments. We also covered the challenges customers face when implementing OPA Gatekeeper at scale across many clusters. To summarize, these challenges broadly fall into two categories:
This post will describe how Rafay’s Kubernetes Operations Platform (KOP) can make it significantly easier to define and manage OPA Gatekeeper policies for Kubernetes using a policy-as-code approach. As deployments scale, the ability to rely on code-based automation to eliminate manual processes and enforce security and governance becomes critical to reduce the risks of human error. A platform like KOP provides tools for customers to natively support policy-as-code. By centralizing both the configurations and ongoing operations for OPA Gatekeeper policies, implementing the desired state with visibility and alerting for violations not only speeds up remediation, but dramatically simplifies kubernetes compliance.
Rafay offers a Cluster Blueprint capability that allows centralized configurations for cluster standardization that can encompass security policies, software add-ons such as service mesh, ingress controllers, monitoring, logging and backup and restore strategies. For example, required controls and software components may vary across development, QA, and production departments. It is incredibly challenging, operationally cumbersome, error-prone, and time-consuming to do this manually. Blueprints address this challenge by ensuring that clusters are always in compliance. Rafay also offers drift detection to protect Blueprint configurations from manual, out-of-band changes (inadvertent or malicious).Software components could be managed add-ons (e.g., OPA Gatekeeper) or custom add-ons. For add-ons like OPA Gatekeeper, Rafay manages the entire lifecycle, including deployment and updates across clusters.
OPA Gatekeeper policies are enforced through Constraints/ConstraintTemplates. When Constraints/ConstraintTemplates (policy controls) are defined and deployed to the cluster, OPA Gatekeeper validates resources during:
The enforcement action (for a policy violation) is specified as part of the Constraint spec with Dry Run, Warn and Deny being the available options.Rafay’s KOP captures detailed audit logs for both Admission requests and Audit Runs making it easier for customers to adopt a crawl (Dry Run), walk (Warn) and run (Deny) approach to orchestrating new policies. On the screenshots below, you can see examples of how these violations are captured:

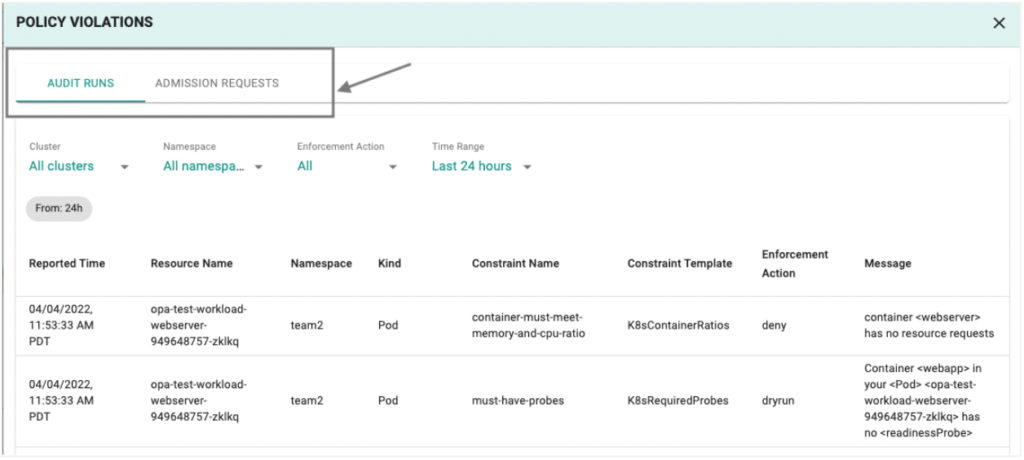
In addition to surfacing violations in a user-friendly manner, Rafay’s KOP also enforces already defined role based access controls (RBAC) to enable selective access to violations. This means that a cluster or a namespace owner will only have visibility into violations for the resources they have been assigned to.
Detailed audit logs are captured for the creation/deployment of policies to clusters and the policy violations. This data can be sent to external monitoring systems (e.g., SIEM tools). In addition, all historical policies are maintained, and this can be used as proof to auditors that the appropriate controls are in place to meet organizational compliance requirements.Rafay’s Kubernetes Operations Platform can help customers operationalize OPA Gatekeeper policies in minutes and altogether remove the need for any continual DIY investment. Policy Management is one of several services that Rafay’s Kubernetes Operations Platform offers, which means that the benefits go significantly over and beyond just managing Gatekeeper policies. If you are ready to leverage the real power of Kubernetes with a platform that provides best-in-class Policy Management capabilities, sign up for a free trial of Rafay today.To learn more about OPA Gatekeeper and Rafay, check out our getting started guide and watch our OPA Gatekeeper demo.

The recently released version of Kubernetes v1. 25 removed the ‘PodSecurityPolicy (PSP)’ capability.
Read Now

As customers scale up their Kubernetes (K8s) environments by adding more clusters and applications, it becomes critical to solve for a consistent, repeatable process to enforce policies and strengthen governance without sacrificing development agility. The OPA Gatekeeper project was conceptualized to provide the necessary tooling to help address this problem.
Read Now