Centrally Manage all the Network Policies for your Kubernetes Infrastructure
Centralized management and visibility into your pod and namespace communication to ensure isolation boundaries and reduce the lateral attack surface fleet-wide, powered by Cilium.
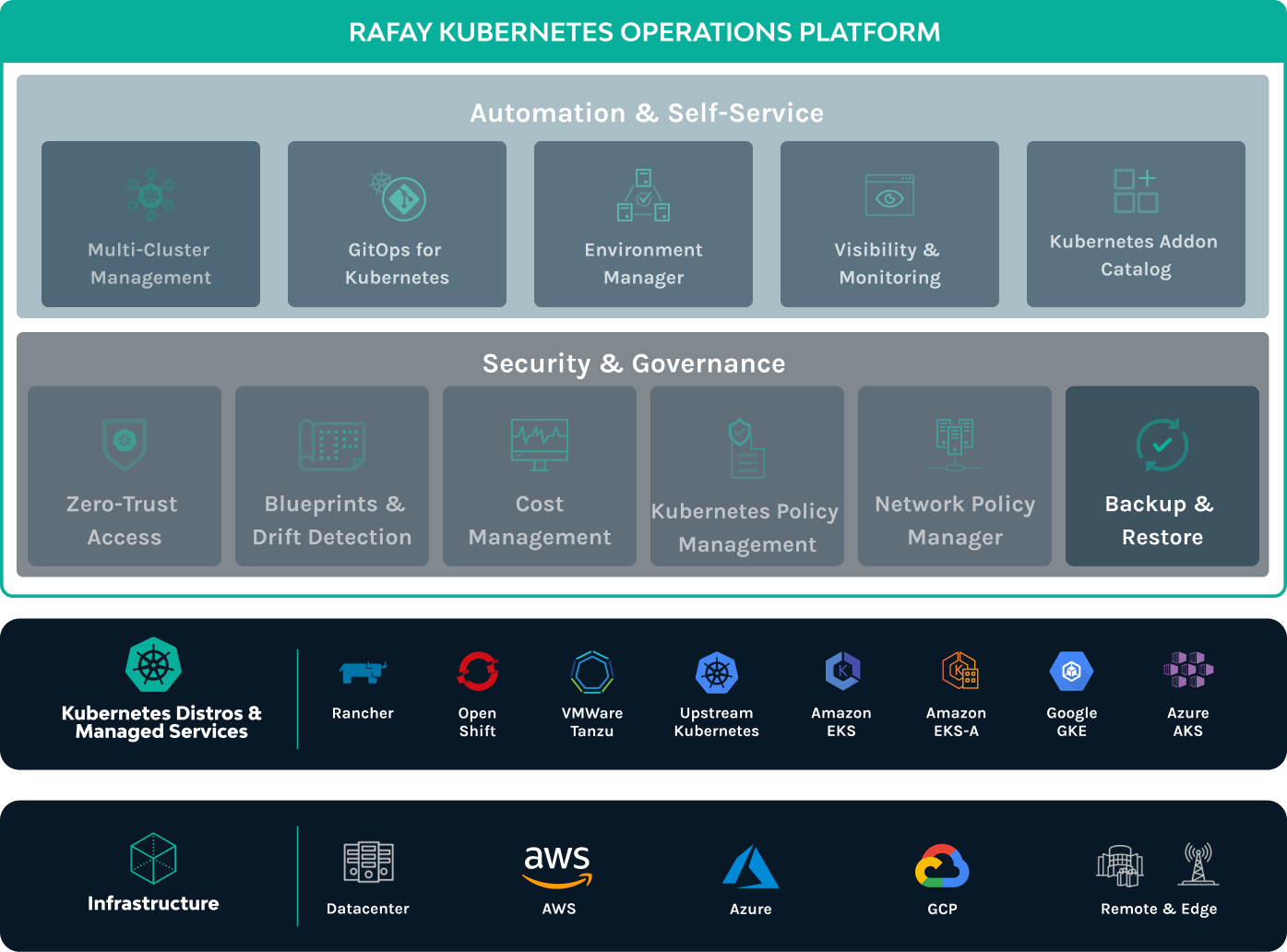
Kubernetes Network Policy Automation, Standardization, and Governance Across Your Fleet of Clusters and Applications, Powered by Cilium
With Rafay, platform teams can configure enterprise-grade Kubernetes network isolation policies and enable developers to gain visibility into traffic flows.

Satisfy security and organizational compliance requirements for isolation and network access
Enable development teams to configure policies for namespace resources and reduce time to resolve issues
Prevent lateral movement and reduce attack surface within and across a fleet of clusters
Visibility Into Real-Time and Historical Network Traffic Flows For Developer Self-Service Based on Assigned Role
Rafay provides real-time network visibility and stores historical traffic flows for your specific namespaces and pods based on role. Enable developers to be self-reliant in debugging network communication flows for their applications while ensuring that platform teams are providing secure identity-based network visibility access based on user and role.
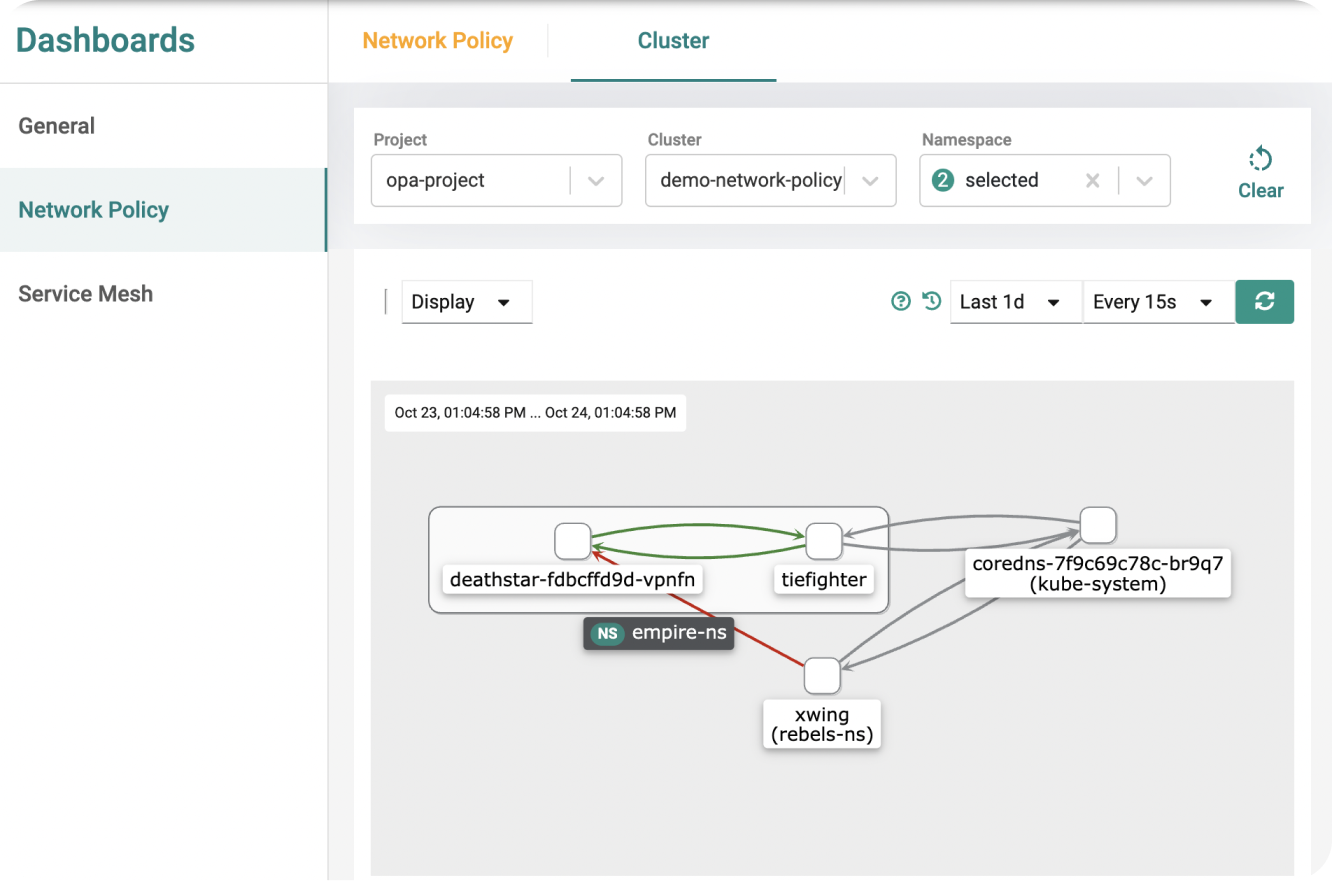
Isolate Communication Between Applications and Namespaces In Both Shared and Dedicated Cluster Environments
In order to reduce the lateral attack surface, Rafay allows you to build policies that can control ingress/egress traffic to clusters and isolate namespaces to implement a zero-trust model into your Kubernetes environments.
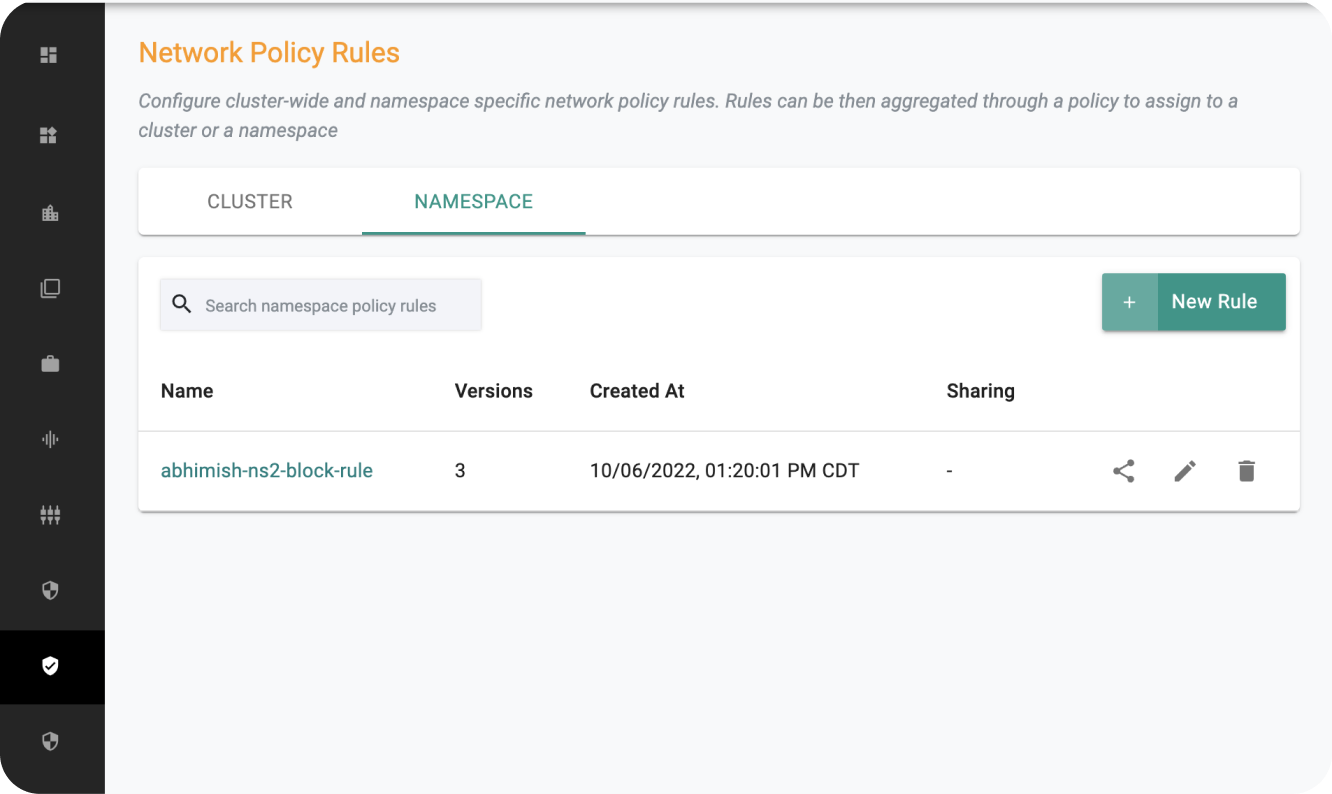
Enforce Network Policy Standards Cluster-Wide and at an Individual Namespace Level
In order to meet security and compliance requirements, it is critical for platform teams to enforce standards that can be met across the organization. For example, platform teams can enforce cluster-wide policies, such as default deny rules or namespace isolation, while leveraging RBAC to enable developers to apply policy rules for their applications that specify the traffic that is allowed to/from pods or namespaces.
See the Network Policy Manager in Action!
Network Policy Management Service FAQs
Rafay Network Policy Management service is fully integrated with Rafay’s platform. Not only does this solve for network security, but other parts of Kubernetes governance, including RBAC, deployment pipelines and infrastructure templates. Additionally, you can increase the reliability and reduce the operational cost with automated deployments, upgrades, and ongoing lifecycle management.
Network policies can be used for workload protection to establish zero-trust and ensure that your applications are only communicating with what is required. In addition, network policies are great for running shared clusters. By creating namespace isolation rules, platform teams are presented with a lightweight option to segment different users and applications from each other during actual runtime.
OPA Gatekeeper is used as a validation engine to ensure that clusters and applications follow a standard protocol tied to configuration. In addition, this can be extended to ensure for example that all clusters have a default network policy.
Network policies meanwhile are used to protect workloads and isolate namespaces during runtime, very much like a firewall. An admin or developer creates network policies that allow/deny communication to other entities.
Best Practices for Securing Kubernetes
Modernize security with zero-trust and role-based access control for your entire fleet. View this white paper now.

Most Recent Blogs
Want Free Access?
See for yourself how to add automation, security, visibility, and governance to your Kubernetes Operations by trying the Rafay Kubernetes Operations Platform!