What is Multi-Tenancy? A Guide to Multi-Tenant Architecture
Multitenancy is a model where teams share infrastructure while keeping data separate. Rafay delivers secure, scalable multi-tenant Kubernetes management.
Read Now
.png)
The Kubernetes community has officially started the countdown to retire Ingress NGINX, one of the most widely used ingress controllers in the ecosystem.
SIG Network and the Security Response Committee have announced that Ingress NGINX will move to best-effort maintenance until March 2026, after which there will be no new releases, no bug fixes, and no security updates. 
A few overlapping forces pushed the community to retire Ingress NGINX.
For years, Ingress NGINX was effectively maintained by one or two volunteers, largely in their spare time. That’s a brutal model for something that sits directly on the edge of thousands of production clusters. Eventually, the responsible thing to do was to stop pretending this was sustainable and set a clear end-of-life timeline.
In 2025, a serious vulnerability CVE-2025-1974 underscored just how dangerous it is to have a heavily-used, under-resourced edge component. Ingress NGINX’s flexibility especially around things like arbitrary snippet annotations — was once seen as a superpower. Over time, those same capabilities turned into hard-to-reason-about attack surface, making it increasingly difficult to secure. 
Ingress NGINX was created when the Ingress API was the only option. Since then, modern requirements have evolved—such as multi-tenancy, advanced routing (headers, canaries, multi-protocol), service mesh integration, and clearer separation of infrastructure and application concerns.
The Kubernetes community responded by designing the Gateway API, a more expressive, role-oriented, and extensible standard.
Once Gateway API hit v1.0 GA and gained multiple high-quality implementations, it no longer made sense to cling to a legacy controller that couldn’t evolve safely. 
The short answer: The GA Ingress API (networking.k8s.io/v1) is not deprecated and remains fully supported in Kubernetes.
The deprecation applies specifically to the ingress-nginx controller, not the Ingress API itself.
At a high level, you have three options:
Below are the available options within the CNCF ecosystem:
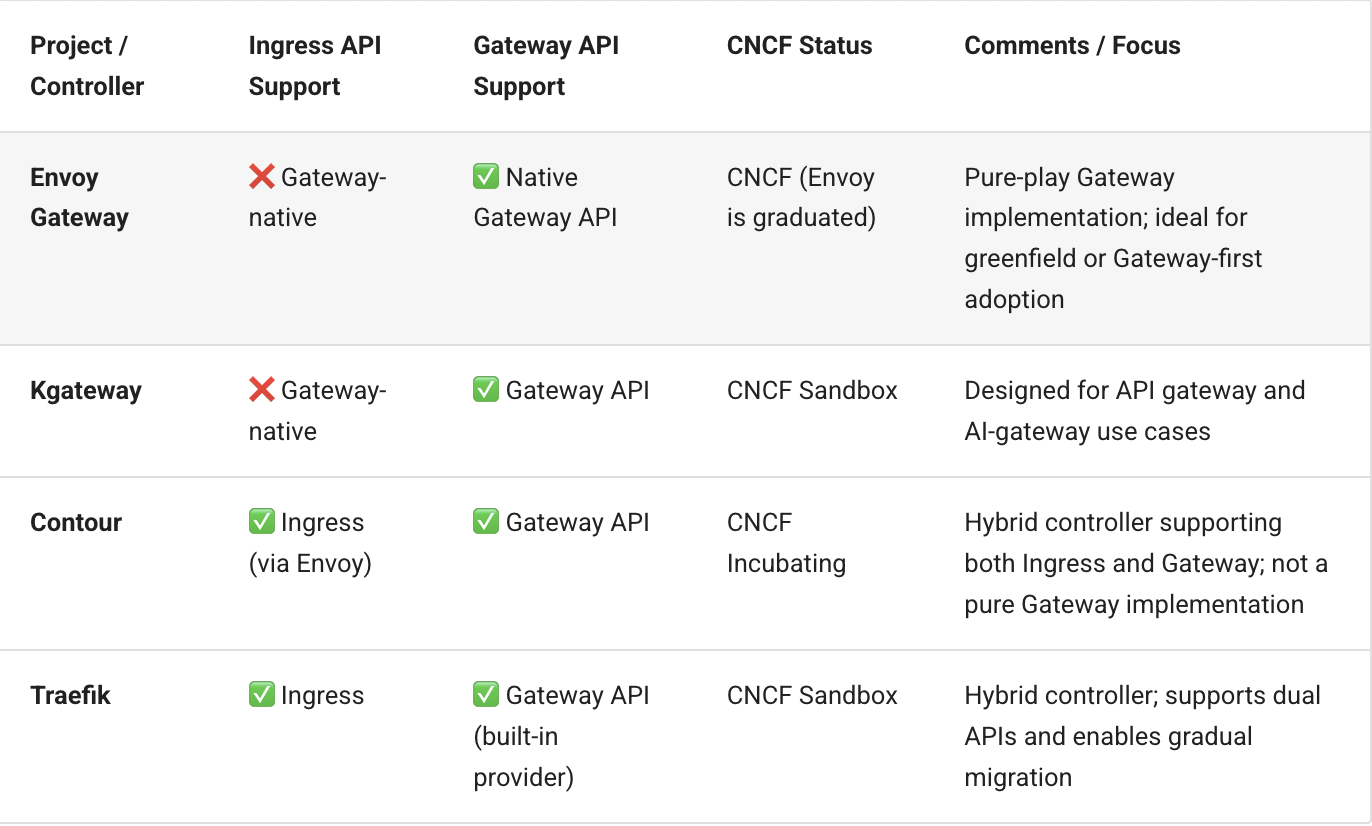
If you prefer to stay in the NGINX ecosystem, F5/NGINX maintains its own open-source NGINX Ingress Controller, which is positioned as a long-term, fully supported alternative to the community ingress-nginx controller. You can continue using the networking.k8s.io/v1 Ingress API, or adopt Gateway API using NGINX Gateway Fabric, their Gateway-native implementation for more advanced scenarios.
If you're already using a service mesh, the simplest path is to leverage the ingress controller that the mesh provides natively.
All of these options support both the Ingress API and the Gateway API, so you can continue using Ingress where needed while adopting Gateway API for new applications or greenfield deployments.
For the migration of the controller from "Ingress NGINX" to "Alternative controller", your timeline essentially looks like the following:
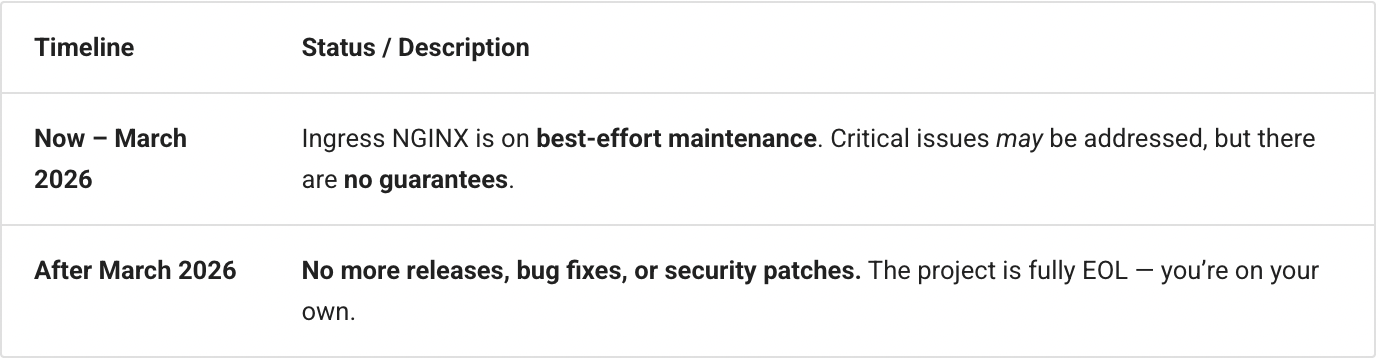
Realistically, if you’re running this in production, you want to be off Ingress NGINX well before March 2026 so you’re not doing emergency edge migrations under pressure.
Before choosing a path, determine whether you plan to:
This choice determines how much change you take on and how quickly.
Migrating fully to the Gateway API requires creating new Gateway resources (Gateway, HTTPRoute, etc.), so it cannot happen in a single cutover. If you choose this path, follow a structured phased migration:
The folks at Traefik have open sourced a migration tool.
If you're not ready to leave the Ingress API yet, the simpler option is to switch to a controller that supports both Ingress and Gateway API. This lets you:
networking.k8s.io/v1 Ingress resourcesControllers that support both APIs include Traefik and Contour in the CNCF ecosystem.
In short: decide whether you want to migrate API + controller together, or start by only replacing the controller. Your timeline and complexity will differ significantly depending on which path you choose.
The deprecation and EOL of Ingress NGINX is definitely disruptive to adopters. But, it is also an opportunity to adopt a more secure, maintainable, and future-proof networking model.
TL;DR for our customers: "Just solve the immediate ingress problem. Migrate to Gateway API on your own timeline with a plan. This is not a crisis!".

Multitenancy is a model where teams share infrastructure while keeping data separate. Rafay delivers secure, scalable multi-tenant Kubernetes management.
Read Now
.png)
This blog details the specific features of the Rafay Platform Version 4.0 Which Further Simplifies Kubernetes Management and Accelerates Cloud-Native Operations for Enterprises and Cloud Providers
Read Now

In this second blog, we installed a Kuberneres v1.34 cluster and deployed an example DRA driver on it with "simulated GPUs". In this blog, we’ll will deploy a few workloads on the DRA enabled Kubernetes cluster to understand how "Resource Claim" and "ResourceClaimTemplates" work.
Read Now